

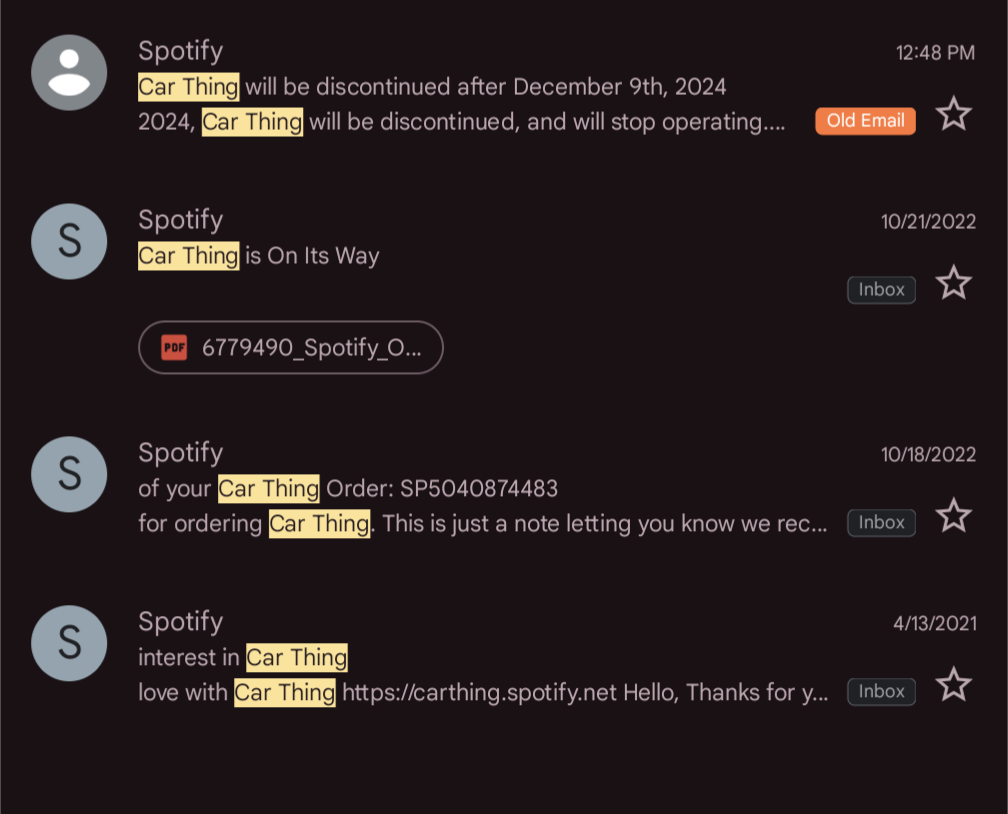
Even Google products have a longer lifespan 😖
I’ve since moved on to Tidal. Bought it at $30 when root mods started to be developed, but never really went anywhere.
Image alt:
- 2021-04-13: Interested in car thing
- 2022-10-18: order placed after discounted to $30
- 2022-10-21: shipped
- 2024-05-23: Discontinue notice
- 2024-12-09: Service discontinued








I have and use a Microsoft account. I would always setup my computer offline because I don’t want my home folder to be called "myema"
il@email.comSeriously who thought that was a good idea? Your account literally has your name tied to it, call it that!