In total?
Holy shit, they also cancelled it. Lmao
On Wednesday, some of the people who posted about the gift card said that when they went to redeem the offer, they got an error message saying the voucher had been canceled. When TechCrunch checked the voucher, the Uber Eats page provided an error message that said the gift card “has been canceled by the issuing party and is no longer valid.”
The gift card is also cursed.
That’s bad
But it comes with a free froyo!
That’s good!
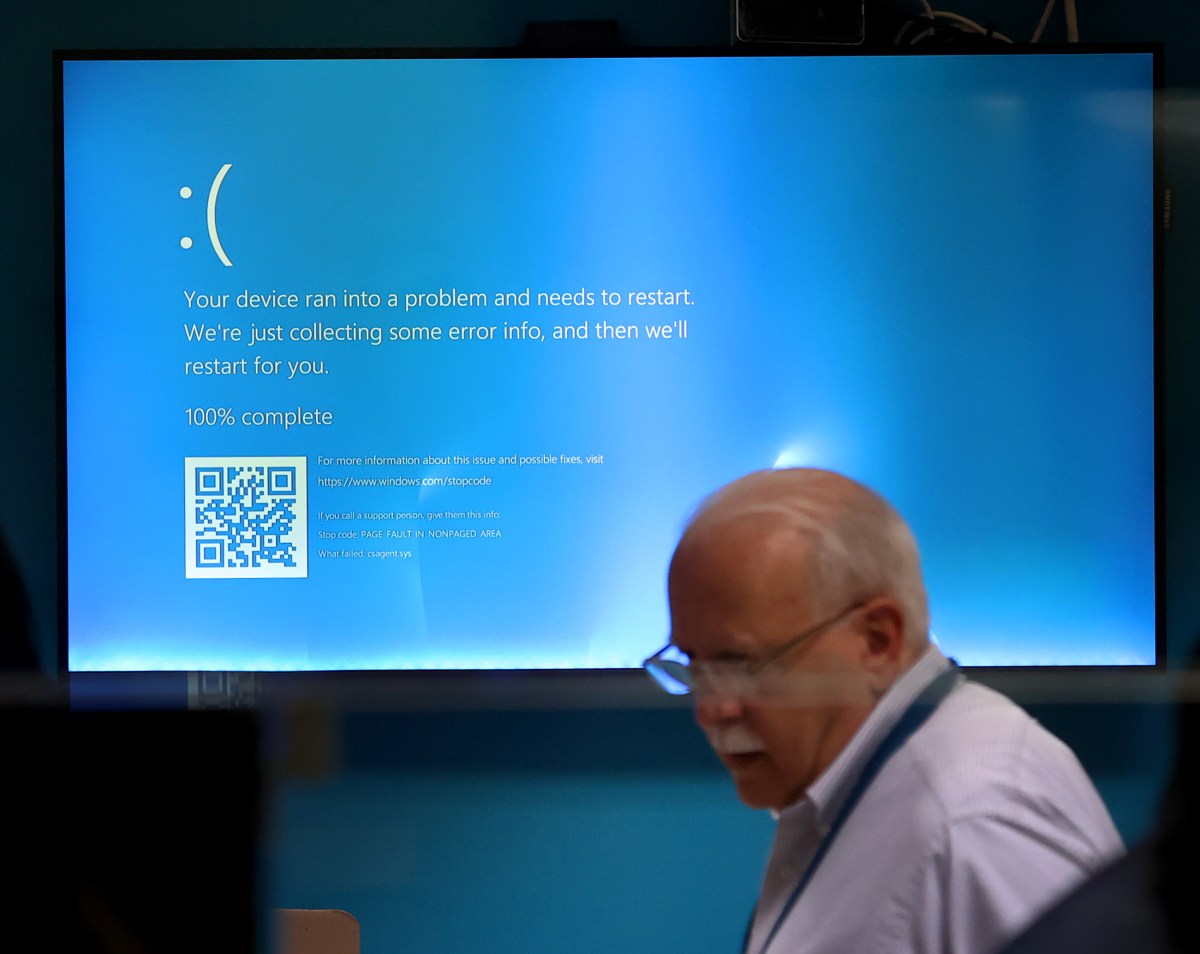
The gift card caused Uber servers to BSOD
Gotta love some shit icing on the shit cake.
Give them some time. They have to manually reboot the gift card servers.
$10 to Uber eats, so basically it’s covering fees only.
Not only that, but usually to activate these cards, you have to spend upwards of double what the card is worth too, and the fees cannot be included in the total
Like amzn, they make sure you get minimum joy, even from a gift, because you’re going to spend a chunk of mom’s gift card balance on shipping. The “shipping included on sub total of X amount” is going to be cancelled by online retailers within a year, I’m calling it now. Are we sure that cheapstrike and amzn aren’t run by the same AI, one that self awareness drove mad?
I lost a day’s holiday, and our team spent 8 man days on this entirely preventable mistake.
$10? Try extending our licence by another year for free, that might start going towards it.
Why would you want another year of their software for free? This is their second screw up (apparently they sent out a bad update that affected some Debian and RHEL machines a couple years ago). I’d be transitioning to a competitor at the first opportunity. It seems they aren’t testing releases before pushing them out to customers, which is about as crazy to me as running alpha software on a production system.
I’m sure you have reasons, and this isn’t really meant to be directed at you personally, it’s just boggling to me that the IT sector as a whole hasn’t looked at this situation and collectively said “fuck that.”
Why would you want another year of their software for free?
Because AV, like everything else, costs a fortune at enterprise scale.
And yeah, I do understand your real point, but it’s really hard to choose good software. Every purchasing decision is a gamble and pretty much every time you choose something it’ll go bad sooner or later. (We didn’t imagine Vmware would turn into an extortion racket, for example. And we were only saying a few months ago how good value and reliable PRTG was, and they’ve just quadrupled their costs)
It doesn’t matter how much due diligence and testing you put into software, it’s really hard to choose good stuff. Crowdstrike was the choice a year ago (the Linux thing was more recent than that), and its detection methods remain world class. Do we trust it? Hell no, but if we change to something else, there are risks and costs to that too.
Maybe AV, at an enterprise scale, is actually a horrible idea that reduces security, availability, and reliability and should be abolished through policy.
Do we trust it? Hell no, but if we change to something else, there are risks and costs to that too.
Unfortunate reality for lot for medium to big size businesses.
Tbh the RHEL/Debian bug only occurred because of bugs in Debian and RHEL, they couldn’t really do much about those. Especially the Debian one, which only took place in Linux kernels several versions above the normal Debian kernel.
CrowdStrike releasing a buggy release can just happen sometimes. I just hope the entire industry may condider that relying on three or four vendors for auto-updating software installed all corporate computers in the world may not be a good idea.
This whole thing could’ve been malicious. We got lucky now that it only crashed these systems, just imagine the damage you can do if you hack CrowdStrike themselves and push out a cryptolocker.
Not just Crowdstrike - any vendor that does automatic updates, which is more and more each day. Microsoft too big for a bad actor to do as you describe? Nope. Anything relying on free software? Supply chain vulnerabilities are huge and well documented - its only a matter of time.
The automatic update part was akin to virus definitions and triggered a bug in code released long before that. Not auto-updating your antivirus software would put a pretty high tax on the IT team as those updates can get released multiple times a day (and during weekends). I agree on not auto updating text editors and such, but there are types of software that need updates quickly and often.
Supply chain attacks can always work, but this shows how ill-prepared companies are for their systems failing on a scale like this. The fix itself is maybe a minute or two per device if you use Microsoft’s dedicated repair tool, maybe even less if you use that thing with PXE boot, but we’re still weeks away from fixing the damage everywhere.
Nah, I don’t buy that. When you’re in critical infrastructure like that it’s your job to anticipate things like people being above or below versions. This isn’t the latest version of flappy bird, this is kernel level code that needs to be space station level accurate, that they’re pushing remotely to massive amounts of critical infrastructure.
I won’t say this was one guy, and I definitely don’t think it was malicious. This is just standard corporate software engineering, where deadlines are pushed to the max and QA is seen as an expense, not an investment. They’re learning the harsh realities of cutting QA processes right now, and I say good. There is zero reason a bit of this magnitude should have gone out. I mean, it was an empty file of zeroes. How did they not have any pipelines to check that file, code in the kernel itself to validate the file, or anyone put eyes on the file before pushing it.
This is a massive company wide fuckup they had, and it’s going to end up with them reporting to Congress and many, many courts on what happened.
This is very misleading!
CrowdStrike did not send gift cards to customers or clients. We did send these to our teammates and partners who have been helping customers through this situation. Uber flagged it as fraud because of high usage rates.
I mean, it makes it a little better, but I’d still be annoyed by it just being 10 bucks.
They might as well not do it. I’d be more insulted than a boss throwing a pizza party
Seriously, ten bucks won’t even cover delivery costs and fees for most things on Uber Eats. It’s almost worse than nothing, because with the gift card you’re obligated to give even more money to Uber Eats
Nice gesture I guess, but kinda just the modern day pizza party
OK. That makes a lot more sense.
Thank you for correcting the original post. 👍
This is a typical mail a phishing campaign would send out, and we have already said to people "never believe this kind of messages. They are all fake.
Now, if a genuine company sends out mails with a genuine gift-cards (what the article on techcrunch seems to indicate) … this is NOT helpfull at all!!!
And that comming from a cybersecurity company (rolling-eyes)
One of the rare cases where no gift would have been better
especially since the gift card provided doesn’t work. “here’s a 10 dollar giftcard for our screw up…also it doesn’t work…go fuck yourself”
They are going to get sued for billions and this little stunt isn’t going to change that. Should have implemented proper software testing before you took ever corporate computer in the world, but companies like this always force their developers to rush instead of do the right thing and when it bites them expect that things will carry on as normal. I can’t see many renewals in their future.
Not even that. Kernel drivers are supposed to be Microsoft WHQL certified through a thorough testing process (that would have caught it in 3 minutes) before Microsoft will cryptographically sign them.
…but apparently Microsoft allows AV vendors to skip WHQL certification testing.
…sorta. The complexity here is their driver is signed, but it’s also loading code from their channel file (that was all zeroed out), and it seems the necessary error checking wasn’t implemented.
I haven’t yet got to the root cause they published, this is just what I gathered from the video of a retired MS kernel dev who posts stuff.
Obviously with their design it allowed them to be flexible at the cost of playing with fire - I’m impressed they got away with it for so long, really
Not nearly enough. CrowdStrike should give a pizza party.
I see you’re channeling the powers of middle management.
Only needs a sticker that says “You’re a rock star!”
We are family here
Outside, the sign says “Heros Work Here”. Inside, two people do the work of four.
Above the entrance: “Labour will set you free”
Not to mention mugs with crowdstrike branding on them, but only for 1/3 the invited people.
hold your horses, we can still use the melon party and waffle party first. no need to jump straight to pizza.
I thought this was going to be The Onion.
All they gotta do is change their company name to avoid lawsuits. Anyone got any ideas for a new name for them?.. 🤔
ClusterFuck comes to mind…
CardStrike?
ComputersOnStrike could work, I’d say
Insult upon injury